1. Introduction
Renewable energy power generation technologies are developed rapidly. The in-stalled capacity and penetration rate of renewable energy in modern power systems are increasing constantly
| [1] | HONG Hanxiao, WU Chenxi, NI Suoyin. Optimal scheduling of new-type power system considering frequency-inertia security constraints [J/OL]. Electric Power Automation Equipment: 1-12 [2024-07-01]. https://doi.org/10.16081/j.epae.202312046 |
[1]
. Renewable energy generation is integrated to power systems with power electronic equipment, which results in decrease of equivalent inertia and increasement of frequency fluctuation after power disturbance in power systems
. Frequency may drop constantly after power disturbance caused by HVDC (High Voltage Direct Curren) transmission blocking, resulting in a large number of loads and units removed, which may lead to instability and collapse of power systems
| [3] | LUO Yazhou, CHEN Dezhi, LI Yiqun, et al. Design of system protection scheme for North China multi-UHV AC and DC strong coupling large receiving-end power grid [J]. Automation of Electric Power Systems, 2018, 42(22): 11-18. https://doi.org/10.7500/AEPS20180529008 |
[3]
. It’s necessary to develop emergency control scheme decision methods to ensure that the margin requirements of security indicators are satisfied to avoid collapse of power systems.
Emergency load shedding is an important measure to ensure the safety of power systems after large-scale power disturbances, which has been studied in many literatures. In the literature
| [4] | CAO Yongji, ZHANG Hengxu, XIE Yuzheng, et al. Configuration scheme of emergency load shedding for HVDC receiving-end power grid based on transient low-frequency and high-voltage features [J]. Automation of Electric Power Systems, 2019, 43(6): 156-164. https://doi.org/10.7500/AEPS20180404006 |
[4]
, “low-frequency high-voltage” characteristics are made full use of to optimize load-shedding control measures after DC blocking. In the literature
| [5] | XU Xin, ZHANG Hengxu, LI Changgang, et al. Emergency load shedding optimization algorithm based on trajectory sensitivity [J]. Automation of Electric Power Systems, 2016, 40(18): 143-148. https://doi.org/10.7500/AEPS20151116002 |
[5]
, transient voltage and frequency safety constraints are comprehensively considered to decide load cutting measures. In the literature
| [6] | SUN Dayan, ZHOU Haiqiang, XIONG Haoqing, et al. Asensitivities analysis based emergency load shedding optimization method for the HVDC receiving end system [J]. Proceedings of the CSEE, 2018, 38(24): 7267-7275+7453. https://doi.org/10.13334/j.0258-8013.pcsee.180127 |
[6]
, the selection method of load cutting point considering transient power angle stability constraints is proposed. On the basis of emergency load shedding, multi-resource coordination control measures to make full use of available control resources are proposed in some literature. A strategy that comprehensively considering HVDC emergency power modulation and load shedding in Literature
| [7] | ZHAO Jinquan, TANG Jianjun, WU Di, et al. Emergency coordination control strategy for transient voltage and transient frequency stability in HVDC infeed receiving-end power grid [J]. Automation of Electric Power Systems, 2020, 44(22): 45-53. https://doi.org/10. 7500/AEPS20191019002 |
[7]
. In literature
| [8] | YUAN Sen, CHEN Dezhi, LUO Yazhou. Stability characteristics and coordinated control measures of multi-resource for DC blocking fault impacting weak AC channel [J]. Electric Power Automation Equipment, 2018, 38(8): 203-210. https://doi.org/10.16081/j.issn.1006-6047.2018.08.029 |
[8]
, characteristics of different control resources is researched to determine the action sequence of multiple types of resources heuristically. In the literature
| [9] | LI Zhaowei, FANG Yongjie, HUANG Hui, et al. Coordinated control of cross-region DC frequency control and emergency power support in system protection [J]. Automation of Electric Power Systems, 2020, 44(22): 31-36. https://doi.org/10.7500/AEPS20200114014 |
[9]
, a coordinated control scheme of DC power modulation and emergency power support considering local and remote information to realize coordinated action among regional power grid systems is proposed. In order to ensure the safety of the receiving end grid with large capacity feed-in DC under severe power disturbance such as DC blocking, it’s important to study the coordinated control of multi-resources
| [10] | BAO Yanhong, FENG Changyou, XU Taishan, et al. Online security and stability comprehensive auxiliary decision making of power system [J]. Automation of Electric Power Systems, 2015, 39(1): 104-110. https://doi.org/10.7500/AEPS20141017001 |
[10]
.
There are a large number of possible future operation modes in modern power systems with high proportion of renewable energy penetration. The traditional “offline decision-making, real-time matching” emergency control measure decision-making only take typical operation modes into consideration, resulting that the developed control measures are difficult to satisfy demands for accurate control.
| [10] | BAO Yanhong, FENG Changyou, XU Taishan, et al. Online security and stability comprehensive auxiliary decision making of power system [J]. Automation of Electric Power Systems, 2015, 39(1): 104-110. https://doi.org/10.7500/AEPS20141017001 |
[10]
. In order to solve the problem that traditional off-line decision-making cannot satisfy the precise control requirements of actual operation mode, some literatures have carried out research on online decision-making of emergency control schemes. In literature
| [11] | WANG Zengping, ZHU Shaoxuan, WANG Tong, et al. Research on stratified optimal load shedding strategy for receiving end power grid [J]. Transactions of China electrotechnical society, 2020, 35(5): 1128-1139. https://doi.org/10.19595/j.cnki.1000-6753.tces.190377 |
| [12] | WANG Changjiang, LI Xiaojing, JIA Chunhe, et al. Trajectory sensitivity based transient voltage two-stage control in AC/DC receiving end system [J]. Electric Power Automation Equipment, 2023, 43(07): 124-132. https://doi.org/10.16081/j.epae.202212023 |
| [13] | ZHANG Zhe, QIN Boyu, GAO Xin, et al. Emergency control strategy of power grid voltage stability based on convolutional neural network and long short-term memory network [J]. Automation of Electric Power Systems, 2023, 47(11): 60-68. https://doi.org/10.7500/AEPS20220712005 |
[11-13]
, it’s proposed to linearize the relationship between transient safety indicators and control quantity based on trajectory sensitivity method, in order to transform the nonlinear emergency control scheme decision problem into a linear programming problem, which can be solved with the linear programming method. In literature
, the decision-making problem of emergency control scheme is transformed into a nonlinear programming problem based on dynamic trajectory information of power system, and the stepwise quadratic programming method is used to solve it. In literature
| [15] | BI Zhaodong, WANG Jianquan, HAN Zhenxiang. A fast load shedding algorithm based on integral sensitivity [J]. Power System Technology, 2002, 26(8): 4-7. https://doi.org/10.13335/j.1000-3673.pst.2002.08.002 |
| [16] | CHEN Qing, ZHOU Haiqiang, ZHU Bin, et al. Coordinated emergency load shedding control optimization algorithm [J]. Power System Technology, 2016, 40(4): 1044-1050. https://doi.org/10.13335/j.1000-3673.pst.2016.04.010 |
| [17] | WANG Tong, LIU Jiuliang, ZHU Shaoxuan, et al. Transient stability assessment and emergency control strategy based on random forest in power system [J]. Power System Technology, 2020, 44(12): 4694-4701. https://doi.org/10.13335/j.1000-3673.pst.2019.0909 |
[15-17]
, in order to avoid the problem that emergency control scheme decision methods based on linear or nonlinear programming methods may not converge in some cases, various heuristic algorithms are applied to make emergency control scheme decision, so as to improve the global convergence of the decision process.
In order to improve the accuracy of the control scheme and ensure the decision-making efficiency of the control schemes, the time-domain simulation and machine learning technologies are comprehensively applied in this paper to propose an emergency control scheme optimization method including pre-optimization and online optimization. In the pre-optimization stage, outputs of new energy and loads are predicted to generate typical future scenarios. Optimal control schemes are obtained based on trajectory sensitivity and machine learning methods, and the schemes are stored into optimization decision knowledge base. In the online optimization stage, the actual operation mode information is obtained, and the appropriate control scheme is selected from the knowledge base as the initial value, for reducing the number of iterations and ensuring decision efficiency. In each optimization iteration, safety indicators are accurately evaluated with time domain simulation to ensure solution accuracy. The effectiveness of the proposed method is verified by an example system.
2. Two-stage Optimization Framework for Emergency Control
2.1. Optimization Model of Multi-resource Coordinated Emergency Control Scheme
The purpose of the multi-resource coordination emergency control scheme optimization is to minimize the control cost
F while ensuring that each security indicator satisfies the margin requirements. In this paper, the frequency and voltage security constraints in the form of binary table in the literature
| [18] | ZHANG Hengxu, LI Changgang, LIU Yutian. Quantitative frequency security assessment method considering cumulative effect and its applications in frequency control [J]. International Journal of Electrical Power & Energy Systems, 2015, 65(65): 12-20. https://doi.org/10.1016/j.ijepes.2014.09.027 |
[18]
are applied, as shown in Eq. (
1):
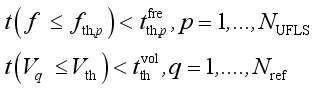 (1)
(1) where
f denotes the system frequency,
fth,p denotes the threshold value of the
pth round Under Frequency Load Shedding (UFLS),
t(
f≤
fth,p) denotes the duration time when
f is lower than
fth,p,
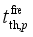
denotes the time delay of the
pth round UFLS,
Vq denotes the voltage of the
qth reference node after DC blocking,
Vth denotes the voltage threshold value,
t(
Vq≤
Vth) denotes the time when
Vq is lower than
Vth,
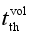
denotes the time threshold value related to voltage security indicator,
NUFLS and
Nref respectively denote the number of rounds of UFLS and reference nodes.
Considering that there are some problems with the traditional binary table method such as poor linearization, this paper refers to the literature
| [5] | XU Xin, ZHANG Hengxu, LI Changgang, et al. Emergency load shedding optimization algorithm based on trajectory sensitivity [J]. Automation of Electric Power Systems, 2016, 40(18): 143-148. https://doi.org/10.7500/AEPS20151116002 |
[5]
to construct the voltage and frequency security indicators as shown in the Eq. (
2). Compared with the indicators in the form of the binary table, the cumulative effects are considered with the defined indicators. Meanwhile, the linearity and smoothness of the indicators are better, which is suitable for sensitivity analysis.
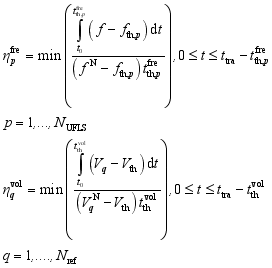 (2)
(2) where
t denotes the time variable,
t0 denotes the time when the disturbance occurs,
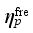
denotes the
pth frequency security indicator obtained based on the frequency-time binary table relevant to UFLS,
fN denotes the rated frequency of the system,
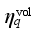
denotes the voltage security indicator of the
qth reference node obtained based on the voltage-time binary table,
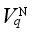
represents the rated voltage of the
qth reference node, and
ttra is the time duration of the considered transient process.
To ensure that the frequency and voltage indicators satisfy the requirements of the corresponding binary table, it’s necessary to ensure that Eq. (
3) is satisfied:
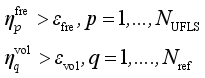 (3)
(3) where εfre and εvol respectively denotes the security indicators margin of frequency and voltage.
The event-driven emergency control is triggered is specifically oriented to specific large-scale power disturbances
| [19] | CAO Yongji, ZHANG Hengxu, ZHANG Yi., et al. Event-driven fast frequency response control method for generator unit [J]. Automation of Electric Power Systems, 2021, 45(19): 148-154. https://doi.org/10.7500/AEPS20210210001 |
[19]
.
In this paper, by solving the optimization problem in Eq. (
3) for the foreseen accident, the emergency control scheme under the corresponding foreseen accident is developed. In this paper, by solving the optimization problem in Eq. (
4), the emergency control scheme under the corresponding predefined contingency is formulated.
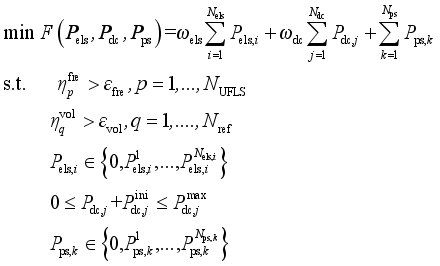 (4)
(4) where
ωels and
ωdc respectively denote the relative cost weighting coefficients of emergency load shedding and High Voltage Direct Current (HVDC) emergency power modulation relative to pump shedding of pumped storage. The priority of multi-resource coordinated control is pump shedding of pumped storage, HVDC emergency power modulation and load shedding in descending order. In this paper,
ωels and
ωdc are taken to be 100 and 10, respectively.
Pels,i,
Pdc,j, and
Pps, respectively denotes loads shed of the
ith load control substation, emergency power modulated of the
jth HVDC, and pump shedding of the
kth pumped storage.
Nels,
Ndc and
Nps respectively denote the number of load control sub-stations, HVDC and pumped storage stations.
Pels = [
Pels,1,…,
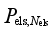
],
Pdc = [
Pdc,1,…,
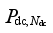
],
Pps = [
Pps,1,…,
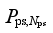
].
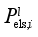
denotes the amount load shedding corresponding to the removal of l feeder lines at the
ith load control substation,
Nels,i denotes the number of feeder lines at the
ith load control substation,
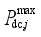
and
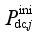
respectively denote the upper limit and the power before modulation of the
jth DC. The amount of pumps that can be cut at each pumping and storage power station constitutes a discrete value set {0,
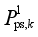
, …,
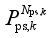
}, where
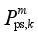
denotes the amount of pumps that can be cut at the
kth pumping and storage power station corresponding to the removal of
m pumping and storage units, and
Nps,k is the number of units at the kth pumping and storage power station.
Equation (
3) is a mixed integer nonlinear optimization problem with both discrete and continuous variables, which needs to be solved by an iterative algorithm. The optimization takes into account the dynamic safety of the system, and in each iteration needs to solve the dynamic safety index based on time domain simulation. If the initial value is not selected properly, the number of iterations is too many to complete the optimization in a short looking time. Reasonable selection of initial value is the key to reduce the number of iterations and speed up online optimization.
2.2. Two-stage Optimization Framework
In order to select reasonable initial values to speed up online optimization and ensure the rapidity of online optimization, this paper proposes a two-stage scheme optimization strategy composed of "pre-optimization" and "online optimization". Firstly, the forward-looking time
T1 and
T2 are first set,
T1>
T2. In the
T1 pre-optimization stage, typical future scenarios are generated based on the prediction of future new energy and load, the corresponding control scheme is solved. Operation mode information of scenarios and control schemes are paired and stored in the optimization decision knowledge base. In the
T2 online optimization stage, accurate information about actual operation modes is obtained. The appropriate scheme in the knowledge base is selected as the initial value, and the optimization scheme under the actual operation mode is obtained by iterative optimization. The flow chart of the optimization strategy for the two-stage scheme is shown in
Figure 1.
Figure 1. Rolling optimization framework of multi-resource coordinated emergency control scheme.
where T denotes time difference between the present moment and the next scheme refreshing moment, ΔT denotes the set time interval.
2.3. Pre-optimization Stage
The frequency of serious power disturbances such as DC blocking is extremely low in the actual operation of the power system, and it’s difficult to collect enough scenario information from the historical operation data of the power system to generate training samples. It’s necessary to construct a set of power system operation scenarios in the offline stage to simulate the frequency dynamics after power disturbances in the time domain, so as to obtain the frequency security indexes such as the maximum frequency deviation of the system under the corresponding scenarios. And then training samples for the training of the frequency security assessment model are generated. Currently, the training sample generation method usually adopts the method of randomly varying the system operating states such as load level and new energy output within a certain range, so as to generate a batch of operating scenarios to construct the training sample set
| [18] | ZHANG Hengxu, LI Changgang, LIU Yutian. Quantitative frequency security assessment method considering cumulative effect and its applications in frequency control [J]. International Journal of Electrical Power & Energy Systems, 2015, 65(65): 12-20. https://doi.org/10.1016/j.ijepes.2014.09.027 |
[18]
. This training sample generation method is difficult to cover the actual operation of the power system, and cannot guarantee the ability of the frequency security assessment model to generalise to the future scenarios to be assessed.. And it will generate a large number of training samples that are far away from the actual operation of the system, resulting in low efficiency of model training.
Generative Adversarial Network (GAN)
| [19] | CAO Yongji, ZHANG Hengxu, ZHANG Yi., et al. Event-driven fast frequency response control method for generator unit [J]. Automation of Electric Power Systems, 2021, 45(19): 148-154. https://doi.org/10.7500/AEPS20210210001 |
[19]
, as a data-driven sample distribution learning method, can learn the sample distribution law without assuming the sample distribution function. In this paper, based on the information of the historical operation mode of the power system, we use the improved Wasserstein Distance Metric-based Generative Adversarial Network (Wasserstein Generative Adversarial Network, WGAN) to learn the distribution law of the actual operation scenario of the system. Then a batch of scenarios in line with the actual operation of the system is generated for time-domain simulation to obtain the frequency security index after the predicted power perturbation event, which is used to construct the training sample set.
2.4. Online Optimization Stage
In the online optimization stage, the time domain simulation method is applied to obtain the dynamic safety index values for scheme optimization. In order to accelerate the iteration speed of scheme optimization, the number of iterations is reduced to ensure that there is sufficient time for time domain simulation in each iteration. From {Ei, 1≤i≤L}, the scheme Esim that is most similar to the optimal control scheme Eact under the actual operation mode is selected. With Esim as the initial value, the scheme is optimized online.
It's difficult to directly select
Esim. Therefore,
Esim is not directly selected in this paper. Firstly, the scenario similarity measure
DS is defined to ensure that similar scenarios correspond to similar schemes with the
DS measure. Based on
DS, the most similar scheme
Ssim is selected from
{
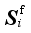
, 1≤
i≤
L}. Then the corresponding scheme in the set {
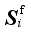
:
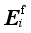
, 1≤
i≤
L} is taken as
Esim. The initial value selection of scheme optimization which is difficult to solve directly is transformed into a similar scenario selection problem which is easy to solve. Reasonable initial value selection can significantly reduce the number of iterations of online optimization. In each iteration there is sufficient time to obtain accurate safety indicators based on time domain simulation to ensure the adaptability of the obtained scheme to the actual operation mode.
3. Solving of Multi-resource Coordinated Emergency Control Scheme
3.1. Iterative Optimization of Control Scheme Based on Trajectory Sensitivity
The optimization problem solved in the pre-optimization and online optimization stage is a nonlinear mixed integer programming problem involving dynamic safety indexes, which is difficult to be solved directly. In this paper, trajectory sensitivity method in
| [4] | CAO Yongji, ZHANG Hengxu, XIE Yuzheng, et al. Configuration scheme of emergency load shedding for HVDC receiving-end power grid based on transient low-frequency and high-voltage features [J]. Automation of Electric Power Systems, 2019, 43(6): 156-164. https://doi.org/10.7500/AEPS20180404006 |
[4]
is used to locally linearize dynamic safety constraints, which are transformed into mixed integer linear programming problems for iterative solution. Local linearization and mixed integer linear programming are continuously solved, and the optimal solution is gradually approached. The iteration process is shown in
Figure 2, where
b denotes the counting variable, representing the
bth iteration.
Figure 2. Rolling optimization framework of multi-resource coordinated emergency control scheme.
Where Pels,b, Pdc,b, Pps,b denotes the control quantity of the control measure after the bth optimization, ΔPels,b+1, ΔPdc,b+1, ΔPps,b+1 denotes the correction at the (b+1)th iteration.
Δ
Pels,b+1, Δ
Pdc,b+1, Δ
Pps,b+1 are obtained by solving the mixed integer linear programming problem in the Eq. (
5):
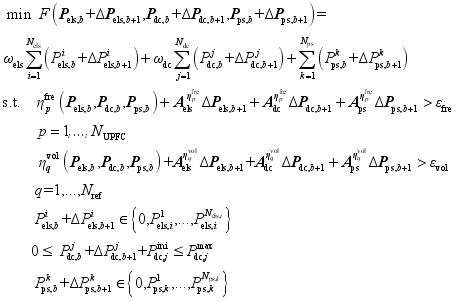 (5)
(5) Where
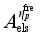
,
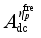
and
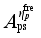
respectively denotes the sensitivity vector composed of the sensitivity of the safety index
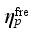
to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station,
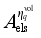
,
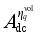
and
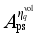
respectively denotes the sensitivity vector composed of the sensitivity of the safety index
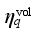
to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station.
According to the convergence criterion in reference
| [5] | XU Xin, ZHANG Hengxu, LI Changgang, et al. Emergency load shedding optimization algorithm based on trajectory sensitivity [J]. Automation of Electric Power Systems, 2016, 40(18): 143-148. https://doi.org/10.7500/AEPS20151116002 |
[5]
, the iterative convergence criterion for optimization of control strategy is that the change of objective function is less than the threshold value Δ
F:
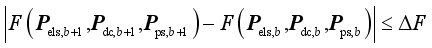 (6)
(6) Or at least one of the safety indicators satisfies the critical value, that is, at least one of the Eq. (
7) satisfies:
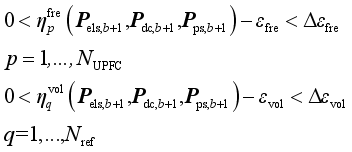 (7)
(7) Where Δεfre, Δεvol denotes the specified convergence threshold, set to a small positive number.
Through the above trajectory sensitivity method, the mixed integer nonlinear programming problem in the pre-optimization and online optimization stage can be transformed into the mixed integer linear programming problem as shown in the equation (
5), so that the mature Benders decomposition method can be further solved
| [20] | TIAN Xichen, GUO Hongye, LI Kexin, et al. Power source planning method satisfying unit cost recovery constraints under market environment [J]. Electric Power Automation Equipment, 2023, 43(05): 252-258. https://doi.org/10.16081/j.epae.202303030 |
[20]
.
3.2. Control Measure Sensitivity Solution
The key to local linearization is to solve the trajectory sensitivity vector. Because of the high dimensional nonlinearity of power system, it is difficult to use analytical method to directly solve the trajectory sensitivity. In this paper, based on perturbation method, the trajectory sensitivity is solved:
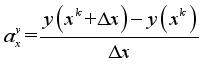 (8)
(8) Where
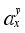
denotes the sensitivity of safety index y to the control quantity x of a control measure, y can be set
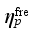
or
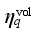
,
x can be the load shed at a load control sub-station, power modulation of a DC, or the cutting pump quantity of a pumping and storage power station,
xk is the value of the control quantity at the kth iteration, Δ
x is the momentum,
y(
xk) denotes the value of safety index
y with the control quantity
xk.
In the pre-optimization stage, multiple iterations of the optimization scheme for a large number of scenarios are carried out. If
y(
xk) is obtained based on time domain simulation in each iteration to calculate the trajectory sensitivity, the calculation time is long, and it’s difficult to ensure that the pre-optimization can be completed within the specified forward-looking time. Therefore, in the pre-optimization stage of this paper, the machine learning model for evaluating
y(
xk) is constructed based on the method described in
| [21] | LI Huarui, LI Changgang, LIU Yutian. Machine learning-based frequency security early warning considering uncertainty of renewable generation [J]. International Journal of Electrical Power & Energy Systems, 2022, 134. https://doi.org/10.1016/j.ijepes.2021.107403 |
[21]
to reduce the pre-optimization time and ensure that it’s completed within the specified forward-looking time.
In the online optimization stage, accurate information about actual operation modes can be obtained. The control scheme can be optimized aiming at the determined scenario. In order to ensure the adaptability of the scheme to the actual operation scenario, the accurate value of y(xk) should be obtained based on the time domain simulation to calculate the sensitivity of the measure. In order to ensure the decision-making efficiency of the control scheme, it is necessary to reasonably select the initial optimization value of the scheme. The relevant content is shown in Section 3.
4. Selection of the Initial Value in the Online Optimization Stage
4.1. Scenario Similarity Measurement
For control schemes E i and E, similarity is measured by Euclidean distance between them, and DE(Ei, Ej) in Section 1 is defined as follows:
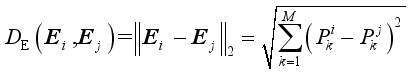 (9)
(9) In the online optimization stage, accurate information about the actual operating scenario
According to the metric DS, similarity between
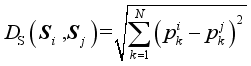 (10)
(10) If
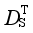
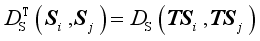 (11)
(11) 4.2. Scenario Similarity Measurement Learning
The key of metric learning lies in the solution of metric transformation matrix
T. The transformation from
Si to
TS i with the metric matrix
T satisfies that for any unequal
i,
j,
k, Eq. (
12) satisfies:
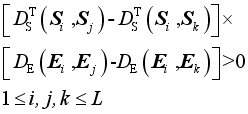 (12)
(12) In this paper,
U in Eq. (
13) is used as the loss function, and the gradient descent method is used to solve the transformation matrix
T:
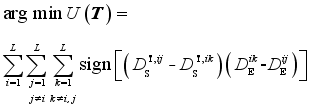 (13)
(13) Where arg min
U(
T) represents the parameter T that takes the minimum loss function
U(
T),
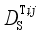
represents
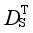
(S i, S
j),
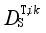
represents
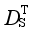
(S i, S
k),
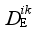
represents
DE(
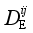
The goal of minimizing the loss function in Eq. (
14) is to ensure that for scenarios
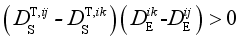 (14)
(14) Where
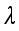
represents the regularization coefficient and
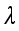
>0.
The optimization problem in Eq. (
13) is solved as shown in
Table 1.
Table 1. Solving process of the optimization problem.
Solving process of the optimization problem |
Step 1 set q=1, seclect the scenario S i and the corresponding scheme Ei |
Step 2 seclect the scenario S j and Sk, satisfying that  < < < < ,( ,( - - )( )( - - )≠0 )≠0 |
Step 3 calculate ( , , , , ) to update T, set q=q+1 ) to update T, set q=q+1 |
Step 4 repeat the above iterative process, until max(| - - |)<ε and |Qq+1-Qq|<μ,1≤m≤N,1≤n≤N, |)<ε and |Qq+1-Qq|<μ,1≤m≤N,1≤n≤N, |
5. Case Study
The simplified provincial power grid in literature
| [21] | LI Huarui, LI Changgang, LIU Yutian. Machine learning-based frequency security early warning considering uncertainty of renewable generation [J]. International Journal of Electrical Power & Energy Systems, 2022, 134. https://doi.org/10.1016/j.ijepes.2021.107403 |
[21]
is used as a numerical example to verify the effectiveness of the proposed method, including about 150 buses and 80 lines. The geographical wiring diagram of the power grid for example is shown in
Figure 3. The base load of the system is 58 GW, and DC #2 with 8 GW power feed in is taken as the disturbance event. DC #1 with 4 GW power and DC #3 with 8 GW power are taken as the controlled DC.
Figure 3. Example grid geographic wiring diagram.
5.1. Evaluation and Validation of Dynamic Security Indicators Based on Machine Learning
The pre-optimization stage is to quickly solve the optimal control scheme in a large number of scenarios, and use the machine learning method to quickly evaluate the dynamic safety indicators. It’s necessary to train the relevant machine learning model in advance, and then solve the multi-resource coordination emergency control optimization scheme based on the method in Section 2. The wind power data used in this paper are 1 month wind power data of 170, 178, 187, 322 nodes of the system and 1 month load data of each load node. Every 10 min is a time section, and there are 4464 time sections in total. In this paper, the prospective time T2=10 mi, T1=1 h.
12 continuous time sections are randomly selected as the refreshing period of the control scheme, and the remaining 4452 time sections are regarded historical data to predict future typical scenarios and generate training and testing samples of the machine learning evaluation model. Based on historical data, 4452 samples are obtained by time domain simulation, 80% as training samples and 20% as test samples. The training and test errors of the obtained machine learning evaluation model are shown in
Table 2. Frequency and voltage security indicators training error root mean square, maximum training error, test error root mean square, maximum test error are shown in
Table 2.
Table 2. Training and test error of machine learning model.
frequency security indicator | 
| 
| 
| 
|
ηfre | 0.0003 | 0.00023 | 0.0007 | 0.00035 |
ηvol | 0.0002 | 0.00016 | 0.00076 | 0.0005 |
It can be seen from
Table 2 that with the constructed machine learning evaluation model, the evaluation error of the constructed machine learning evaluation model for frequency and voltage safety is small and within the allowable range.
5.2. Validation of Optimization Accuracy of Control Scheme at Pre-learning Stage
L is set 200 in Section 1, and the scenario generation method in Reference
| [21] | LI Huarui, LI Changgang, LIU Yutian. Machine learning-based frequency security early warning considering uncertainty of renewable generation [J]. International Journal of Electrical Power & Energy Systems, 2022, 134. https://doi.org/10.1016/j.ijepes.2021.107403 |
[21]
is used to generate 200 typical future scenarios. The method in Section 2 is used to solve the control scheme under each scenario, and the scenario information and corresponding control scheme are stored in the knowledge base. Iterations, values of security indicators and costs of schemes are shown in
Table 3. In this example, margin of voltage security indicators is large, and the dominant security factor is frequency security indicator
ηfre. Therefore, only
ηfre is shown here.
As shown in
Table 3, with the method proposed in this paper, cost of control schemes can be reduced while the security indicators satisfying the requirements. The comparison between the optimization control solution of trajectory sensitivity calculated based on machine learning model and trajectory sensitivity calculated using time-domain simulation method is shown in
Table 4, where
Ptotal represents the control quantity,
tcal represents the
calculation time.
Table 3. Values of each index in the iteration process.
NTra | NBend | 
| 
| F |
0 | \ | -0.11313 | -0.11352 | 0 |
1 | 7 | 0.08523 | 0.08576 | 381.1 |
2 | 9 | 0.02134 | 0.02154 | 365.2 |
3 | 13 | 0.00751 | 0.00731 | 321.6 |
4 | 6 | 0.00103 | 0.00128 | 313.2 |
Table 4. Comparison between machine learning and time domain simulation methods for trajectory sensitivity.
evaluation method | Ptotal | tcal | F | ηfre |
machine learnig | 5.61 GW | 12.5 s | 313.2 | 0.00128 |
time-domain simulation | 5.49 GW | 3818.2 s | 297.4 | 0.00101 |
The time for calculating the dynamic security indicators with time-domain simulation method is about 214.6 h, which is much longer than 1 h prospective time. By using the machine learning method to calculate the dynamic security indicators, the total time required to solve the control scheme under 200 scenarios is only 27.3 min within the 1 h forward-looking period.
5.3. Comparison of Optimization Process Under Different Initial Values in Online Optimization Stage
When entering the forward-looking period of 10 min, it’s necessary to match the scene that is most similar to the actual operation mode as the initial value, and iteratively optimize to obtain the optimal control scheme.
λ is set 0.1,
ε and
μ are respectively set 0.075 and 300. The training process converges after about 32 generations, and the training time is only 141.2 s. The similarity between the future scene and the actual scene is measured based on
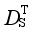
, and the most similar scene obtained by using
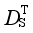
measurement is the 119th scene.
Ptotal,
tcal,
NTra,
NBen,
F and
ηfre obtained based on different measurement are shown in
Table 5, where
Nsce represents the selected scenario number. Ten random initial values are selected to optimize the scheme, and the average value of each initial value is compared with the optimized scheme obtained in this paper.
Table 5. Comparison of optimization results under different initial value selection schemes.
selection method | Nsce | Ptotal/GW | NTra | NBen | tcal/s | F | ηfre/×10-3 |
random | / | 5.41 | 8 | 45 | 2303 | 288 | 1.02 |
DS | 34 | 5.42 | 5 | 22 | 1089 | 289 | 1.03 |

| 119 | 5.41 | 2 | 3 | 136 | 287 | 1.02 |
As shown in
Table 5, compared with
DS, with the measurement proposed in this paper a better initial value can be provided for the iterative optimization of the control scheme in the actual operation mode. The number of optimization iterations can be reduced, ensuring that the online optimization of the control scheme can be completed within 10 min foresight time.
5.4. Comparison with Other Methods
The optimization method of emergency control scheme in this paper is further compared with the Random Forest (RF) model in literature
| [22] | FU Junpeng, CHEN Xiuhong, GE Xiaoqian. Uncorrelated linear discriminant analysis with L2,1-norm regulation and its application in face recognition [J]. Computer Engineering & Science, 2017, 39(02): 343-350. https://doi.org/10.3969/j.issn.1007-130X.2017.02.019 |
[22]
and the Convolutional Neural Network in
| [23] | CAO Zhen, ZHUANG Jun, XUE Jinhua, et al. Optimization of emergency control strategy for frequency of receiving-end power grid under DC blocking based on improved particle swarm optimization and hybrid convolutional neural network [J/OL]. Modern Electric Power: 1-12. [2024-02-01]. https://doi.org/10.19725/j.cnki.1007-2322.2023.0132 |
[23]
, as shown in
Table 6.
Table 6. Comparison of optimization results with different optimization methods for emergency control schemes.
frequency security indicator | the two-stage optimization method | RF | CNN |
Ptotal | 5.41 GW | 7.27 GW | 5.02 GW |
tcal | 136.7 s | 3.2 s | 2.1 s |
F | 287.6 | 389.9 | 221.8 |
ηfre | 0.00102 | 0.00278 | 0.00089 |
Compared with the other two methods, in the two-stage optimization method proposed in this paper, time domain simulation is used to solve the corresponding security indicators in the online optimization stage, which ensures the accuracy of the calculation results. In the final optimal control scheme, the system safety index ηfre is 0.00102, which meets the corresponding requirements, and the control cost of the obtained control scheme is small. At the same time, the initial values are provided for the online optimization stage at the pre-optimization stage, which improves the optimization efficiency and reduces the optimization time. Although the final optimization time is 136.7 s, which is higher than 3.2 s of the RF method and 2.1 s of the CNN method, it’s still far less than the stipulated prospect time of 10 min in the online optimization stage, ensuring that the scheme optimization can be completed within the stipulated 10 min prospect time.
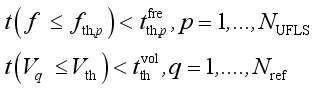 (1)
(1) 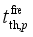 denotes the time delay of the pth round UFLS, Vq denotes the voltage of the qth reference node after DC blocking, Vth denotes the voltage threshold value, t(Vq≤Vth) denotes the time when Vq is lower than Vth,
denotes the time delay of the pth round UFLS, Vq denotes the voltage of the qth reference node after DC blocking, Vth denotes the voltage threshold value, t(Vq≤Vth) denotes the time when Vq is lower than Vth, 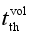 denotes the time threshold value related to voltage security indicator, NUFLS and Nref respectively denote the number of rounds of UFLS and reference nodes.
denotes the time threshold value related to voltage security indicator, NUFLS and Nref respectively denote the number of rounds of UFLS and reference nodes.  (2)
(2) 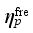 denotes the pth frequency security indicator obtained based on the frequency-time binary table relevant to UFLS, fN denotes the rated frequency of the system,
denotes the pth frequency security indicator obtained based on the frequency-time binary table relevant to UFLS, fN denotes the rated frequency of the system, 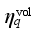 denotes the voltage security indicator of the qth reference node obtained based on the voltage-time binary table,
denotes the voltage security indicator of the qth reference node obtained based on the voltage-time binary table, 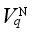 represents the rated voltage of the qth reference node, and ttra is the time duration of the considered transient process.
represents the rated voltage of the qth reference node, and ttra is the time duration of the considered transient process. 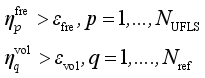 (3)
(3) 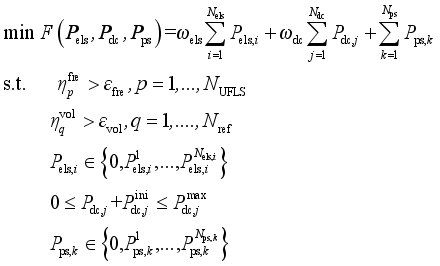 (4)
(4) 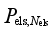 ], Pdc = [Pdc,1,…,
], Pdc = [Pdc,1,…, 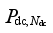 ], Pps = [Pps,1,…,
], Pps = [Pps,1,…, 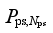 ].
]. 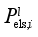 denotes the amount load shedding corresponding to the removal of l feeder lines at the ith load control substation, Nels,i denotes the number of feeder lines at the ith load control substation,
denotes the amount load shedding corresponding to the removal of l feeder lines at the ith load control substation, Nels,i denotes the number of feeder lines at the ith load control substation, 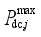 and
and 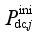 respectively denote the upper limit and the power before modulation of the jth DC. The amount of pumps that can be cut at each pumping and storage power station constitutes a discrete value set {0,
respectively denote the upper limit and the power before modulation of the jth DC. The amount of pumps that can be cut at each pumping and storage power station constitutes a discrete value set {0, 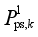 , …,
, …, 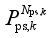 }, where
}, where 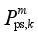 denotes the amount of pumps that can be cut at the kth pumping and storage power station corresponding to the removal of m pumping and storage units, and Nps,k is the number of units at the kth pumping and storage power station.
denotes the amount of pumps that can be cut at the kth pumping and storage power station corresponding to the removal of m pumping and storage units, and Nps,k is the number of units at the kth pumping and storage power station. 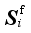 , 1≤i≤L}. Then the corresponding scheme in the set {
, 1≤i≤L}. Then the corresponding scheme in the set { 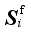 :
: 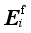 , 1≤i≤L} is taken as Esim. The initial value selection of scheme optimization which is difficult to solve directly is transformed into a similar scenario selection problem which is easy to solve. Reasonable initial value selection can significantly reduce the number of iterations of online optimization. In each iteration there is sufficient time to obtain accurate safety indicators based on time domain simulation to ensure the adaptability of the obtained scheme to the actual operation mode.
, 1≤i≤L} is taken as Esim. The initial value selection of scheme optimization which is difficult to solve directly is transformed into a similar scenario selection problem which is easy to solve. Reasonable initial value selection can significantly reduce the number of iterations of online optimization. In each iteration there is sufficient time to obtain accurate safety indicators based on time domain simulation to ensure the adaptability of the obtained scheme to the actual operation mode. 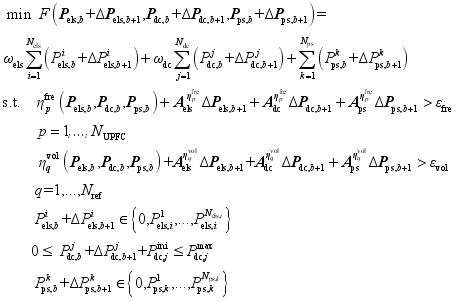 (5)
(5) 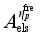 ,
, 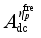 and
and 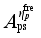 respectively denotes the sensitivity vector composed of the sensitivity of the safety index
respectively denotes the sensitivity vector composed of the sensitivity of the safety index 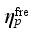 to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station,
to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station, 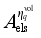 ,
, 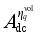 and
and 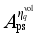 respectively denotes the sensitivity vector composed of the sensitivity of the safety index
respectively denotes the sensitivity vector composed of the sensitivity of the safety index 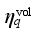 to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station.
to loads shed at each load control sub-station, power modulation of each DC, and pump shedding of pumped storage at each pumping and storage power station. 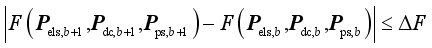 (6)
(6) 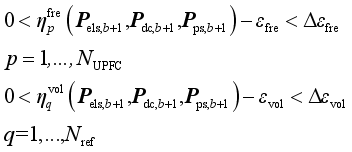 (7)
(7) 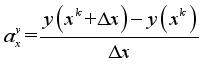 (8)
(8) 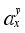 denotes the sensitivity of safety index y to the control quantity x of a control measure, y can be set
denotes the sensitivity of safety index y to the control quantity x of a control measure, y can be set 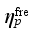 or
or 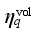 , x can be the load shed at a load control sub-station, power modulation of a DC, or the cutting pump quantity of a pumping and storage power station, xk is the value of the control quantity at the kth iteration, Δx is the momentum, y(xk) denotes the value of safety index y with the control quantity xk.
, x can be the load shed at a load control sub-station, power modulation of a DC, or the cutting pump quantity of a pumping and storage power station, xk is the value of the control quantity at the kth iteration, Δx is the momentum, y(xk) denotes the value of safety index y with the control quantity xk. 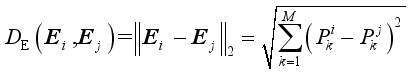 (9)
(9) 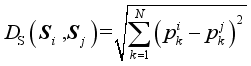 (10)
(10) 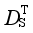
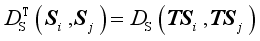 (11)
(11) 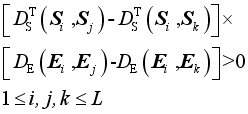 (12)
(12) 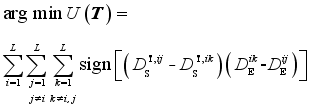 (13)
(13) 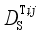 represents
represents 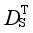 (S i, S j),
(S i, S j), 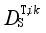 represents
represents 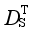 (S i, S k),
(S i, S k), 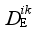 represents DE(
represents DE( 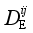
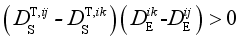 (14)
(14) 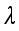 represents the regularization coefficient and
represents the regularization coefficient and 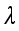 >0.
>0. 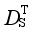 , and the most similar scene obtained by using
, and the most similar scene obtained by using 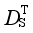 measurement is the 119th scene.
measurement is the 119th scene.